Network Security
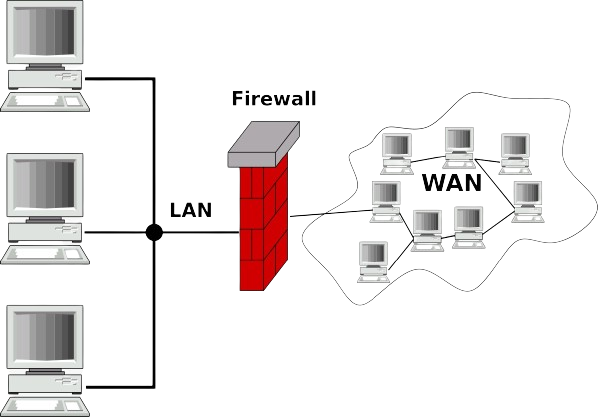
Firewall
You’ve heard of firewalls, but what are they really for? Do they stop viruses? Can you manage without one?
Actually, there’s a good chance that you are using a firewall right now — if your computer is running a modern operating system, there will be one built in, or else your security suite features a firewall.
Network Upgrading
You need to carefully identify key weaknesses in your current WLAN architecture and design ways to address them. This includes ensuring the right equipment is in the right place so that your
WiFi users have the best connection experience with the lowest amount of interference and congestion. It’s also important to look at the types of WiFi devices connecting to the network in order to address accessibility and security.


Cyber Security
Multiple cyber-attacks and compromise of personal information of millions of people globally show that the complexity and intensity of cybersecurity attacks are on the rise, and it could have broader political and economic ramifications.
As cybercrimes become more lucrative and cybercriminals become smarter, cybersecurity too will have to be intelligence driven, enabling a swift response to the advanced attacks. As breaches get harder to detect, the stakes for protecting one’s organization from cyber threats will get higher this year.



